Define scope of investigation - identify target person and threat context
At the beginning, we define the scope of investigation together with you. Depending on the threat scenario, the social environment - such as publicly visible interactions or connections - may be included in the analysis, but only to draw conclusions about the target person. A targeted analysis of friends or family members is not conducted.
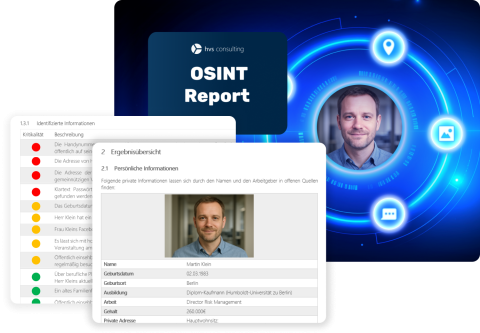
For the initial research, we usually require only a few details: In many cases, name and employer are sufficient - information typically already available as part of the assignment. Based on this, we start the systematic evaluation of publicly accessible sources to create a meaningful profile of the target person.
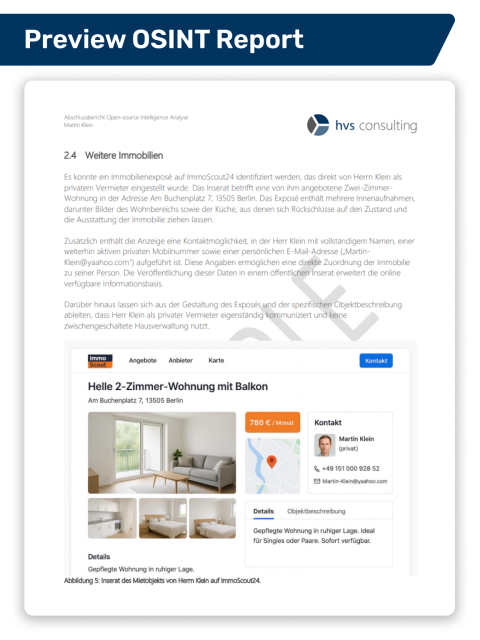
If, during the process, a targeted reverse search becomes necessary - for example, to verify whether certain data (e.g., email addresses or phone numbers) appear in known data leaks, or to simulate what an attacker could do with additional personal information - we will coordinate this with you. If you have not yet provided such data or if we have not identified it during research, you can supply it as needed.
Individual threat situations or specialized risk factors can be communicated in advance - they will then be considered with increased attention in the further analysis.