Complete encryption within 48 hours
Complete encryption within 48 hours

We, the HvS IR team, handled a ransomware incident, where “INC Ransom” deliberately destroyed data and provided false information during negotiations. Furthermore, the ransomware group exploited a vulnerability in the FortiGate firewall from January 2025 (FG-IR-24-535). In this article, we share our findings and provide recommendations.
The attack was based on typical attack techniques, known vulnerabilities and widespread misconfigurations and thus fits into the typical pattern of ransomware attacks. Nevertheless, the attackers managed to completely encrypt the environment within 48 hours after the initial access. Several valuable lessons may be learned from the incident:
Due to a recent misconfiguration in the firewall, the management interface was exposed to the internet. The firewall has been vulnerable for a longer time, but the vulnerabilities could not be exploited from the internet until that point. For this reason, we have been preaching for years that critical vulnerabilities must be patched promptly, regardless of whether the affected device or an affected service is accessible via the internet. A small configuration error can change everything, as in this case.
Our various analyzed FortiGate incidents show that threat actors often use the following approach:
Our negotiations with INC Ransom and the attack context revealed interesting results:
Active Directory misconfigurations and weaknesses very often lead to a rapid domain compromise and allow ransomware actors quick and efficient exfiltration and encryption activity. In this case it took the attackers only 48 hours from initial access to full encryption. That's simply far too fast.
This attack highlights once again: security is not a product, it’s a process. Don’t rely on a single appliance exposed to the internet. Protection against ransomware attacks needs a security-in-depth approach with a variety of prevention, detection, and response measures. Missing one of these three pillars will likely lead to a fast compromise with almost no chances for an adequate reaction.
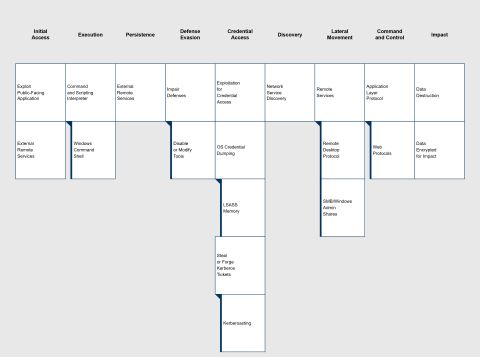
INC Ransom gained initial access by exploiting the FortiGate firewall vulnerability FG-IR-24-535 (FortiOS 7.0.15). At an unknown point in time, the management interface of the unpatched firewall was accidentally exposed to the internet. The exploit allowed the attackers to create a malicious super_admin account. They then set up an SSL VPN configuration and used it for remote access to the victim’s network. The breached FortiGate was further abused to extract credentials of the Active Directory user configured for the RADIUS authentication (see FG-IR-19-007 for further details). This account allowed them to perform further analysis of the Active Directory domain and to locate weak configurations or vulnerabilities. Subsequently the actor performed a Kerberoasting attack and cracked the password of the built-in Domain Administrator account, which was also configured as a service principal for single service installations.
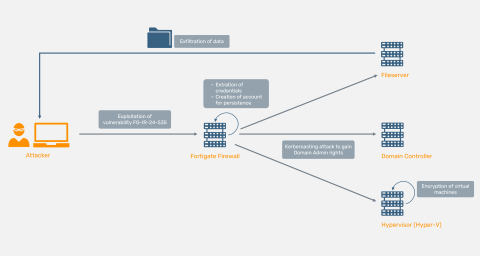
With domain admin rights, INC Ransom moved laterally through the network using the Remote Desktop Protocol. They accessed the victim’s fileserver and exfiltrated well over 10000 files. Within 48 hours of the initial breach, the attackers deployed their ransomware on Hyper-V servers, using a variant of their crypter named win.exe. This caused widespread outages as most virtual machines were encrypted. In some cases, the actor had to manually execute the ransomware within a VM or even delet entire HyperV volumes. It is assumed that these workarounds were taken, when VMs could not be stopped or filesystem locks were not bypassed. Finally, a Meterpreter-based remote access trojan was executed on a hypervisor, likely as a fallback access method or to monitor the ongoing encryption.
To access directly via our MISP feed, use the following link:
Alternatively, the IOCs are listed in the following table:
| IOC Type | Indicator | Notes / Comment |
|---|---|---|
| ip-dst | 185.174.100.204 | C2 channel of svchost.exe meterpreter sample |
| url | http[://]185.174.100.204:443/L7RZw57VJ-b1dfR0k_tCyQtB1fJI8WowHQJSk54rTfUI2od24XrEIUzV5WGzx5fD0nPOwbVMrUfjFtDSZ8s8FudwarDyt7dL8gMPumRtXRv_ondaA99DiB1AmQDhTROOEB5RNqoBUGF7RO1eVLkzN4bgXoa9mjeqRlP1HJkpzxwa-XWfCySg54DfgGxSZPQAlpmdrTQwiPTmXmZzxGfhQBf | svchost.exe meterpreter C2 URI |
| sha1 | 6e45db2cc4648a388fbd6f3d82c7da9c8e30187d | svchost.exe meterpreter sample |
| filename | svchost.exe | svchost.exe meterpreter sample |
| md5 | 2f000e0a52d6ee0c89f93fa5ab4c7e3c | svchost.exe meterpreter sample |
| sha256 | cf1ebd6fb534d65dd0e8164db9693988d5a4a645dd044beba578ab25c0033e66 | svchost.exe meterpreter sample |
| text | %PROGRAMDATA%\Microsoft\ | svchost.exe meterpreter sample |
| sha1 | 41b9a2ca27188c967a28a9b72950380cd0fa8e20 | win.exe INC RANSOM crypter |
| filename | win.exe | win.exe INC RANSOM crypter |
| sha256 | ef8bb466a368d5f564d05b54aea154b117847938c07627e85e3eb0e147296644 | win.exe INC RANSOM crypter |
| text | \Users\Administrator\Documents\x64 | win.exe INC RANSOM crypter |
This ransomware incident demonstrates how quickly attackers can exploit known vulnerabilities and misconfigurations in organizations. The main issues were insufficiently patched systems, misconfigured Active Directory environments, and inadequately monitored user accounts.
The article highlights that early detection and preventive measures are crucial to limit the impact of such attacks. Detailed threat information and early indicators, as provided in HvS Threat Insights, can help identify risks in time and prevent security incidents.

Head of Incident Response
With extensive experience in analyzing and managing a wide range of security incidents, Moritz Oettle, Head of Incident Response at HvS-Consulting, possesses deep expertise in containing, mitigating, and following up on cyberattacks.
Co-Head of Incident Response
He has extensive experience in incident response and digital forensics for DAX-30 and FTSE-500 companies. Marc feels at home in two worlds — offensive security and incident response: While he focuses on analyzing and resolving security incidents in his day-to-day work, he’s not hesitant to use hacking tools himself during purple-team exercises.
